Securing My Home Lab

Taking Control
Lately, amidst the whirlwind of spending time with my family, starting a new job, staying committed to my studies, and tending to my Home Lab, I've embarked on a journey to fortify my network. I recently introduced a managed switch into my setup, setup VLANs for specific use cases, and configured firewall rules to ensure airtight separation and protection for various devices, VMs, and services. I'll be dedicating a separate post to shed light on my newly revamped network and how I intend to utilize the different VLANs I'm currently crafting.
Along with all this, I feel like I've come up with a good work flow in setting up new VMs, securing them, installing the services I need, and securely accessing those services from outside my network when necessary and I wanted to share my current environment and some things I do to secure my homelab. I do want to begin working with scripting this process or using automation tools for creating these servers, I'm sure it'll turn into days of going down the rabbit hole, after which I'll write a blog post about it.
Pi Hole and Pi Alert
My quest for more control over my network and my deep-seated aversion to ads led me to Pi Hole, a solution I'd known about for some time but had never implemented till now.
Pi Hole operates as a DNS sinkhole, employing lists sourced from various places to block connections to advertising URLs and tracking sites. You can customize and add block lists to your instance to customize what you are blocking. Here's a site that has a good amount of block lists: Pi Hole Block Lists.
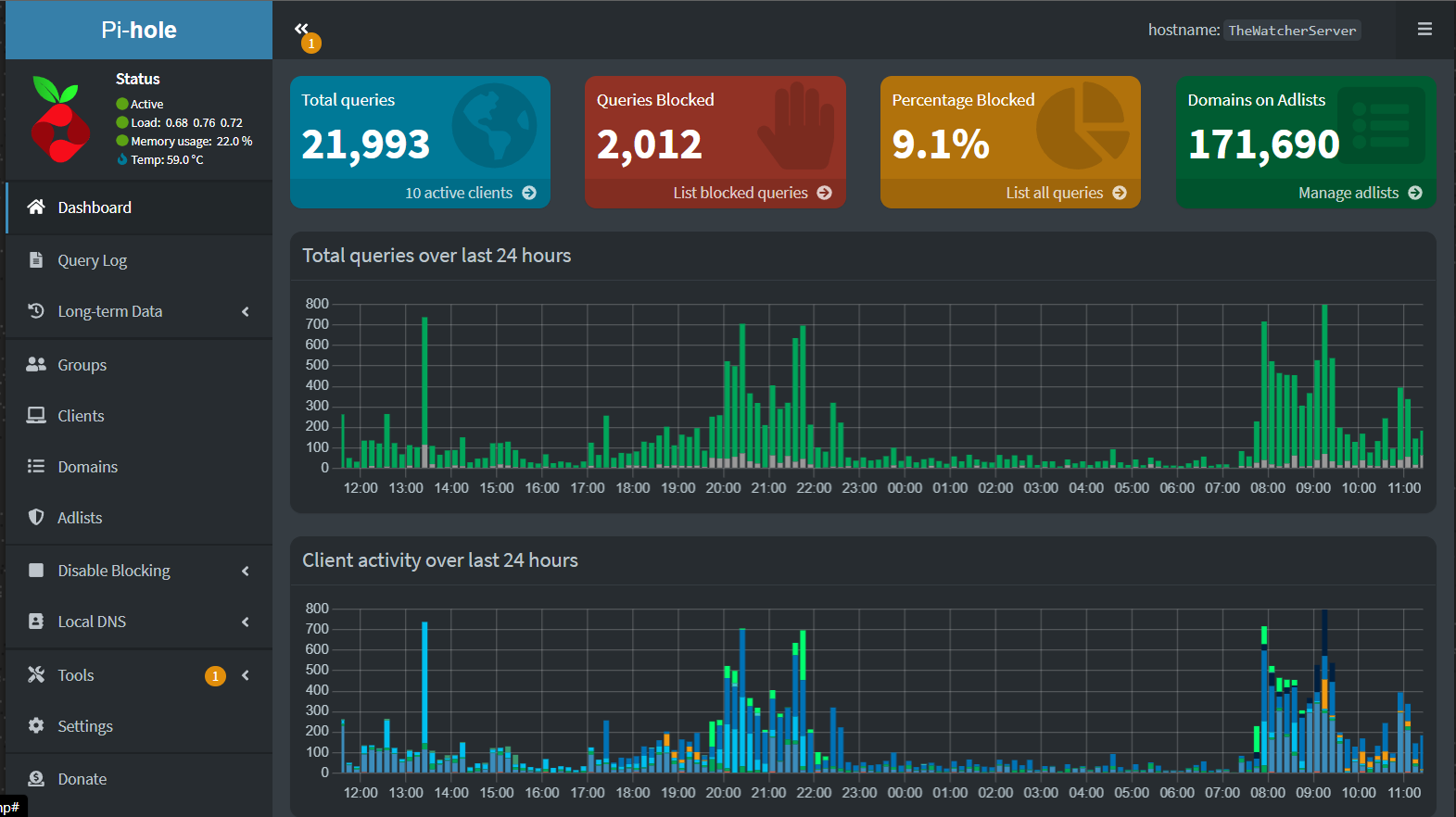
In addition to Pi Hole, I've embraced Pi Alert, a tool that keeps tabs on current and newly connected devices within your network. It includes tools to manage and investigate the devices connected to your network, providing an excellent means of oversight.
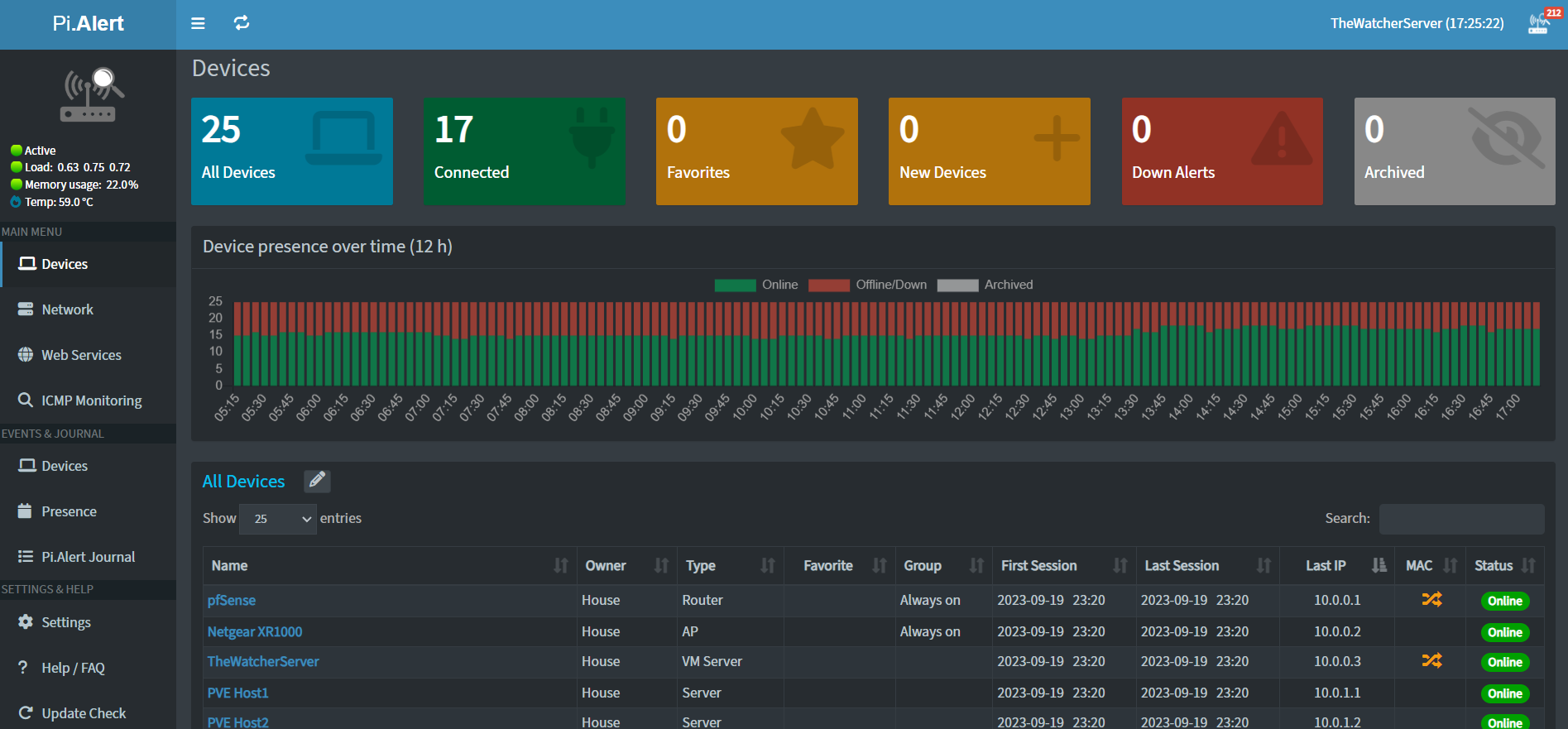
I installed these two on the same LXC within Proxmox as I could not get the Docker version to work correctly. If you decide to go this route, I have a note to get past one issue I ran into here.
Another option I've yet to explore in detail is pfBlockerNG within my pfSense Router, but I'll be sure to share an update when I do.
Server Security & Hardening
For many of my VMs running different services, I rely on Ubuntu Server as the primary OS. These self-hosted applications serve both internal and external needs. To secure these applications for external access, I've employed various techniques like reverse proxies (NGINX and Traefik), virtual IPs using Kemp Load Balancer, and more recently, Cloudflare tunnels. These options not only make the setup process quick and straightforward but also minimize the need to poke holes in my router/firewall.
When it comes to connecting to, managing, and configuring the Linux VMs, SSH remains my go-to. I particularly appreciate the “feel” and aesthetics of the Windows Terminal app, which I use on my Windows 11 laptop for server connections.
Secure access is very important, so I've put in place measures to ensure that while I can log in, others are kept out. It's important to not allowing repeated login attempts,, effectively thwarting brute-force attacks. I opt for long, intricate passwords for login, and I've compiled a checklist of other configuration changes for securing and hardening the OS.
IDS/IPS (Work in Progress)
While fortifying each VM, I also wanted enhanced oversight over what is happening across my network. This led me to explore various open-source IDS/IPS software packages, aiming to have more control over my homelab.
My journey began with setting up Snort on my pfSense firewall, a fairly straightforward process. I'm still in the process of testing out different rule sets and discovering an entirely new world of information and learning.
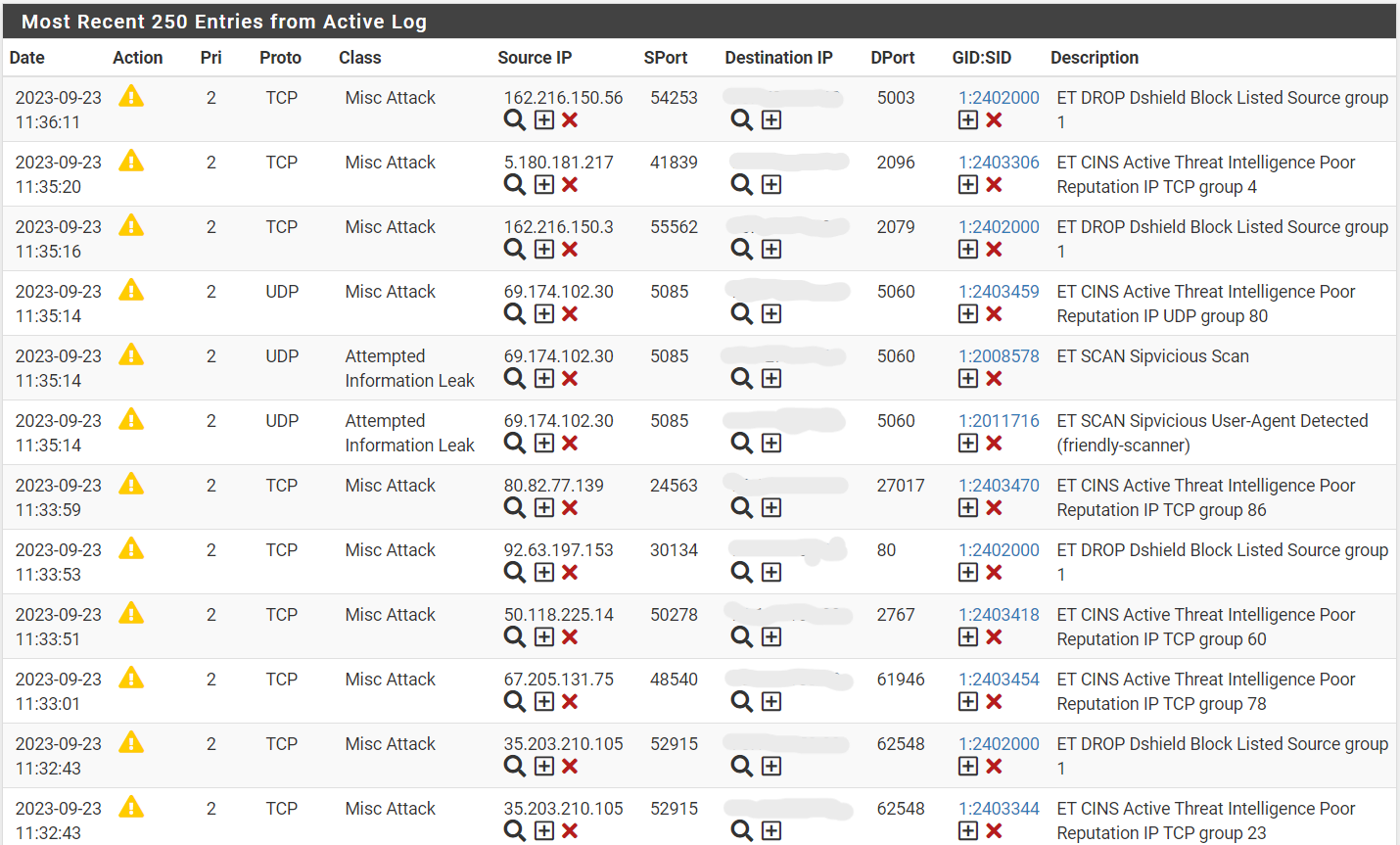
Shortly after, I ventured into testing Suricata as well, but it requires more fine-tuning before I activate any blocking features.
With my network's defensive capabilities taking shape, I stumbled upon a video from NetworkChuck about Wazuh, an open-source Security Information and Event Management (SIEM) system brimming with so many features. After diving into the video and delving into Wazuh's documentation, I installed it and began exploring its features.

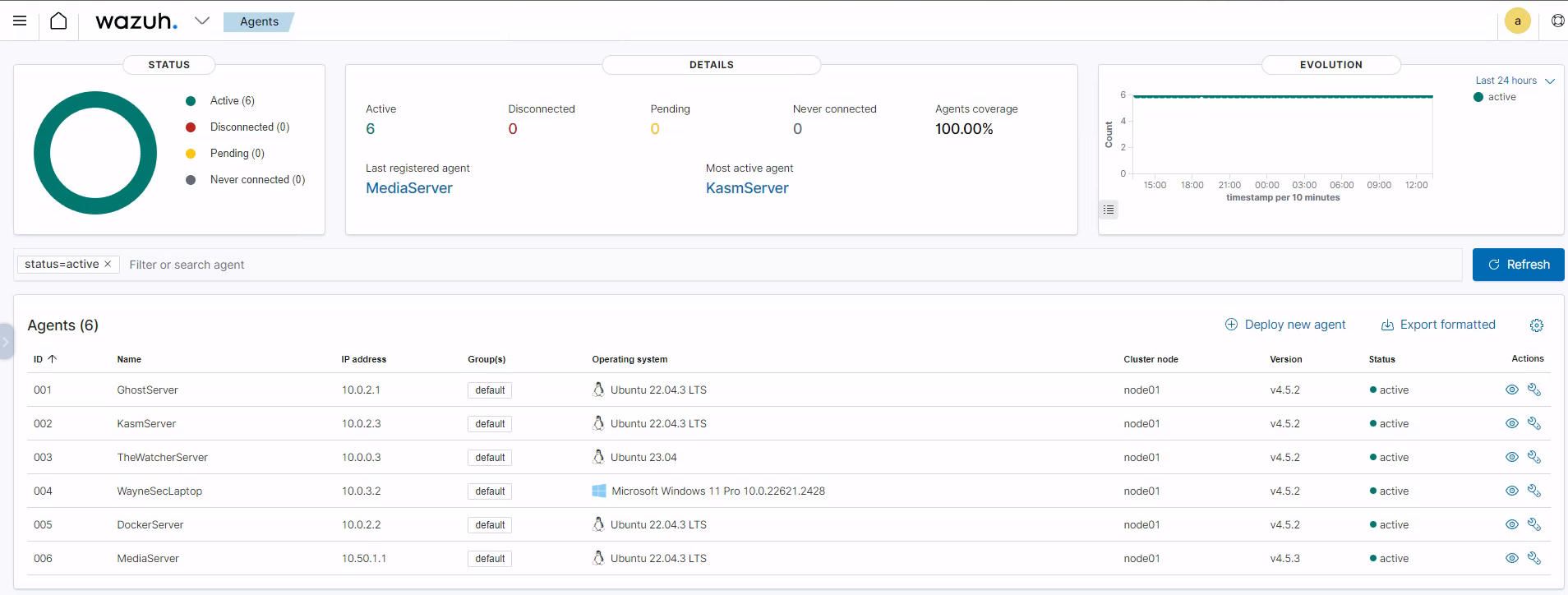
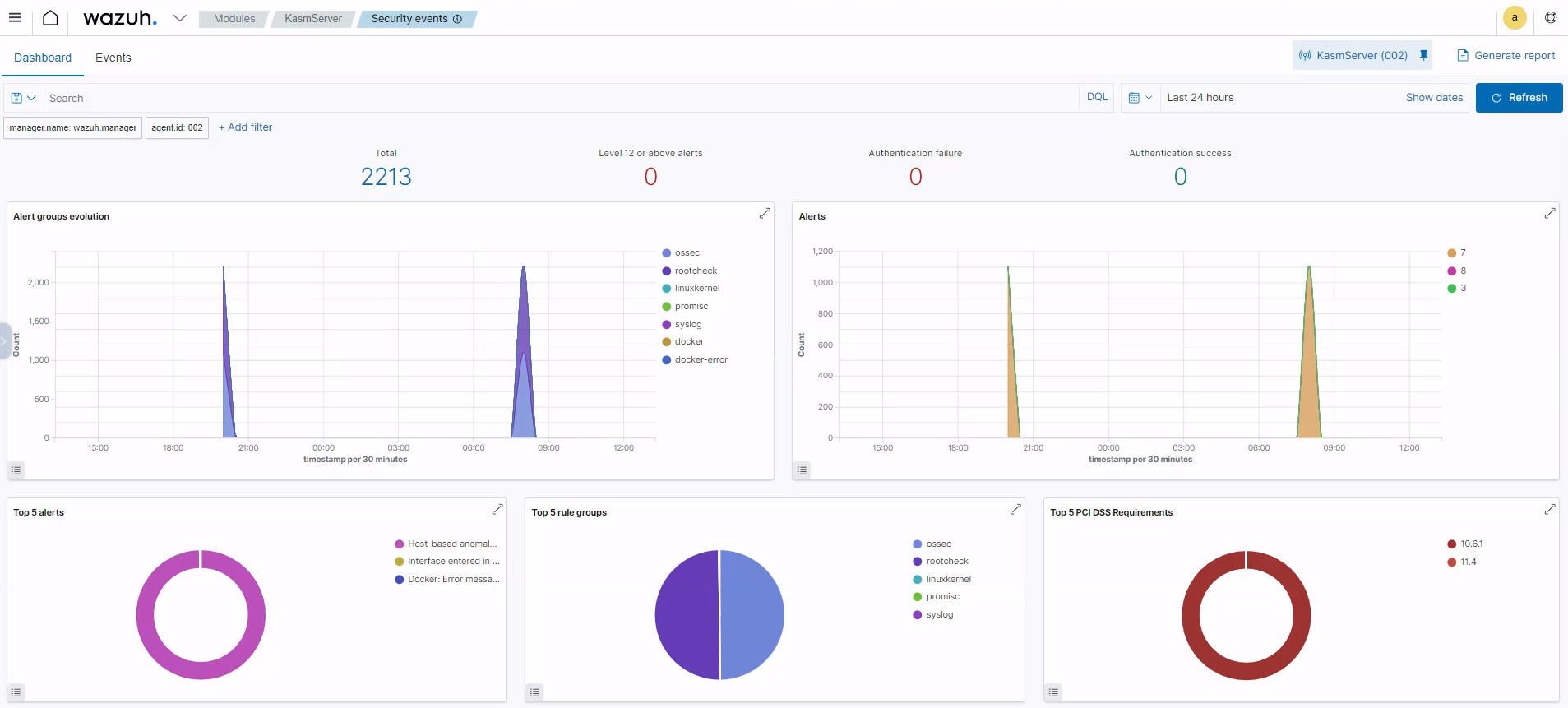
I must say, Wazuh has made it significantly easier to monitor all the devices on which I've installed its agent. The depth of information it presents, coupled with its configurable features, is truly remarkable. I'm still in the early stages of acquainting myself with Wazuh, but the ability to aggregate logs and have a comprehensive view of all my machines is nothing short of amazing.
As I become more familiar with Wazuh, you can certainly expect a post about its setup and features in the future.
Thank you for reading todays post, I hope you have a great day!
