End of the year Wrap-up

Intro
It's been a while since I've provided an update on all the things happening in my home lab. Moving forward I'll be doing better at documenting as I go, but the excitement of completing a task or finally figuring something out tends to take over, especially after hours or days of banging my head against a wall trying to figure things out. Nonetheless, I want to keep up with documenting changes and updates to my setup. So, here's an overview of everything I've been working on recently, ensuring you're caught up before I dive into more detailed posts.
Managed switch modification
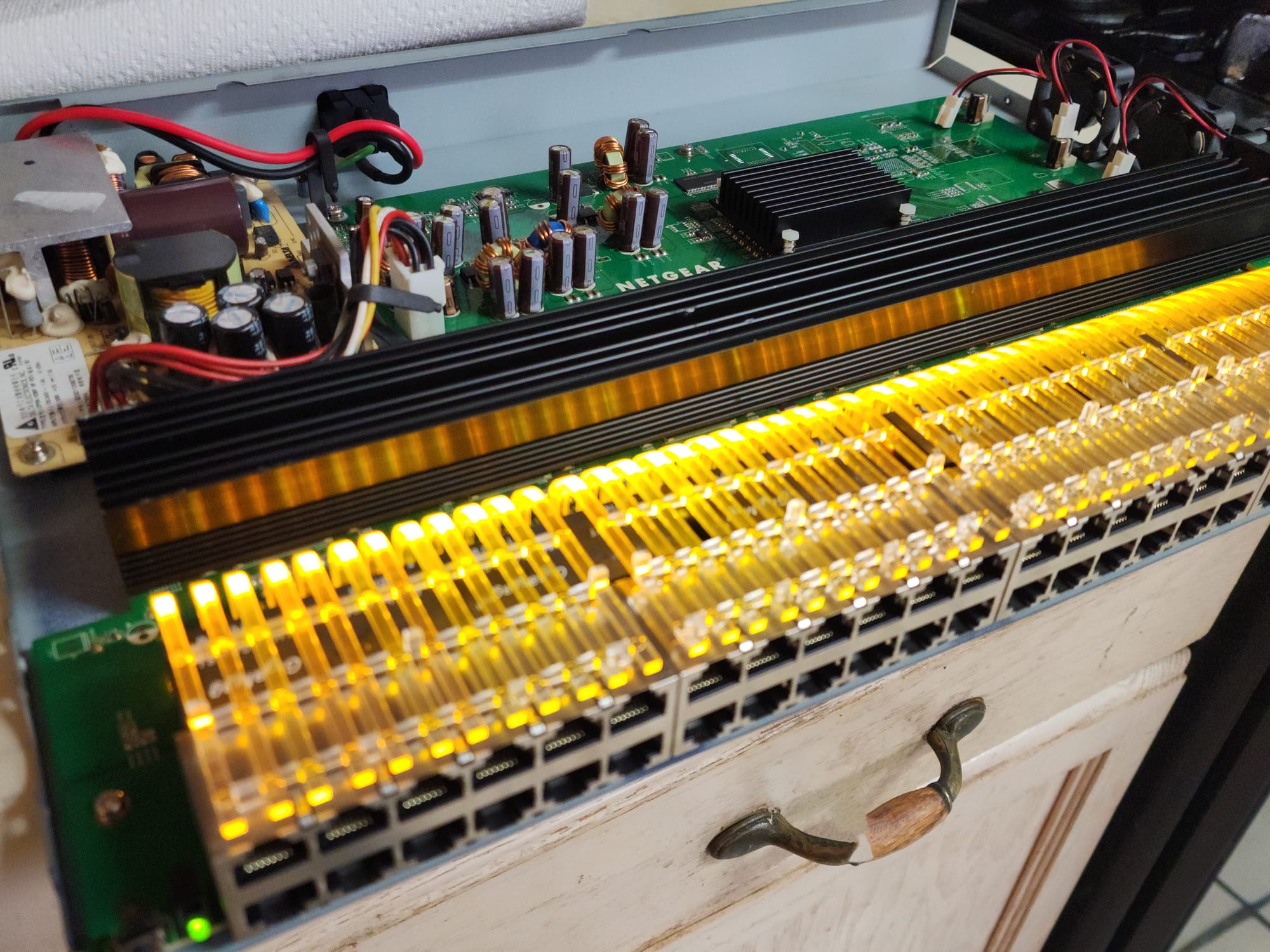
In a previous post I mentioned that I had purchased a Netgear 48-port GS748T v3 managed switch but couldn't use it since my setup was in my room and the fans were much too loud for that environment. This switch was a great find for $50 and It has opened up many more areas of tinkering and learning.
Instead of purchasing quieter fans, I chose to cut a large hole into the top of the case and install a pc fan I had laying around. I used an angle grinder to cut the hole which didn't come out as bad as I thought it was going to. I drilled out the mounting holes to mount it to the case. With a small modification to the connector I was able to plug directly into the old fan's port and it's very quite and has better airflow. Once configured and installed I was able to segment my network which opened my homelab up to so many new possible configurations.

pfSense custom DNS setup for PiHole
In a previous post I mentioned how I used PiHole and PiAlert to gain more control over my network. Before I had VLANS setup, both of these were amazing to have running on my network, I really enjoyed using PiHole for blocking ads and PiAlert for letting me know when new devices had joined my network.
I recently stopped using both and removed the CT they were running on in Proxmox. After setting up VLAN's (Next Section) and not wanting to open ports between them for the devices to access the CT running the PiHole and PiAlert I removed them. I am currently playing with pfBlocker-NG as a replacement for Pihole but I would like to fine tune to get it where I feel comfortable to allow it to block connections or requests. PiAlert will definitely be coming back to monitor new devices connected to my Wi-Fi and possibly other VLANs.
I did want to mention the best way I found to assign your own custom DNS server within pfSense. Once you have both PiHole and PiAlert up and running, you can set them as your DNS server by adding the their IP address to the DNS setting under Services/DHCP Server/"Interface Name" instead of just adding it to System/General Setup which is how I saw more than a few tutorials setting this up. This way, any new devices connecting to that Network interface will be given PiHole as it's DNS server during the DHCP process.
VLAN setup
Okay, setting up VLANs was more work than I initially expected, mainly because there were gaps in my knowledge when I started getting everything configured. During this setup phase, I attempted getting LAGG setup but was unsuccessful so I will return to that at another time. I really want to understand why things don't work so I can fill in those gaps in my knowledge I mentioned before. The amount of ethernet ports I had available was a limiting factor. This is something I will remedy in the near future by purchasing another 4 port network card for my newer Proxmox server. In a pinch, I could also use some USB to ethernet dongles but I haven't had the need yet.
Once I planned out which VLANS I wanted to setup, I began creating them with segregation in mind. I wanted no traffic to pass between the VLAN's by default, only the connections I allow. I will not be going over the setup process here, maybe in a future post when I can get LAGG working so I can include everything I've learned from using pfSense. It was a learning process, especially learning how VLAN tags work when configuring the switch, pfSense, and configuring network settings for VM's in Proxmox.
Current VLANs
DMZ - Used for externally accessed services such as Plex, Blog, Kasm, and all other Docker testing. I still have no ports open as I utilize Cloudflare Tunnels for accessing these services. I initially intended for my services to run on a different VLAN called SRVC VLAN but did not have enough network ports, so they all ended up on this VLAN
CyberArena - Used for learning about network monitoring, pentesting, red/blue team tactics, and running a honeypot (I actually just finished running T-Pot Honeypot on this VLAN for 3 days and will be analyzing the data and making a post soon). This VLAN has it's own dedicated ethernet port to only be used by these VM's on this network to limit any chances of something gaining access to my other networks.
Wi-Fi - Used for Wireless devices including game systems, phones, and TV's - Do not want anyone with Wi-Fi access to my Wi-Fi network to be able to access any of my homelab services. I also have a guest Wi-Fi for anyone visiting my home.
MGMT - Used for only the Proxmox Servers as the management network. - Originally intended for this to include the my managed switch and wireless AP but currently the only devices connected are my Proxmox servers themselves. All VM's or CT's are assigned to the other VLAN' s (Network Ports) depending on their usage.
Benefits of VLAN's
I don't know how I ever worked without VLAN's in the past. Security and control are the main benefit to having my network segmented into VLANs. I have control over each network through firewall rules that are tailored and customized based on what connections I want to make. Wi-Fi devices are isolated to their own VLAN, all the services running on my DMZ network are isolated as well. My DMZ machines are also hardened just after creating them and as well as being monitored by Wazuh (Dedicated VM) and SNORT (Package on pfSense).
I avoid opening any public facing ports and use Cloudflare tunnels for accessing all my internal services I would like to access from outside my network. Even with all this, I still have the confidence of knowing if anyone were to gain access to one of my VM's on this network, are stuck in the DMZ and cannot get to my other networks or devices.
CyberArena - My hacking playground
My CyberArena VLAN has been invaluable for my learning as I am able to build, configure, and install victim and attack machines to practice network scanning, finding and exploiting vulnerable services and open ports, and playing with Active directory, all without risking any of my other services or machines.
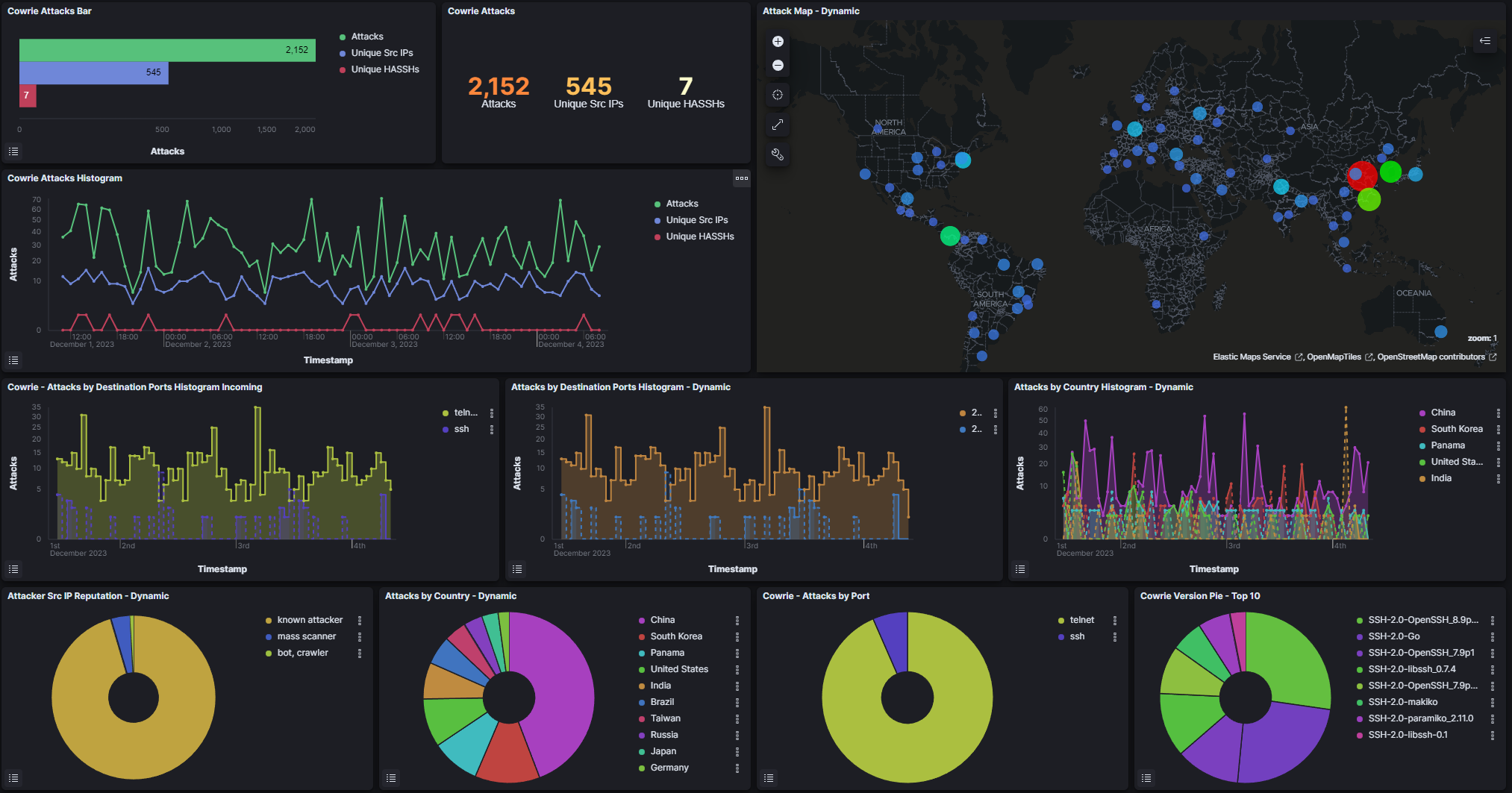
Recently I decided to run a honey pot called T-Pot Honeypot which is an amazing tool for spinning up 20+ honeypots. Included are a host of security tools that collect and log data such as IP addresses, usernames and passwords used in brute forcing attempts, commands typed when attackers gain access, and malware and file collection. T-Pot also comes with some amazing visualizations (graphs, tables, and live attack maps) using the Elastic Stack.
I really wanted to run this in the cloud for security reasons but the system requirements were way to high and I did not want to spend any money on this project. I decided I could run on my newly created CyberArena VLAN as long as I have some well written firewall rules to keep network traffic contained. I use my older server to run these machines and nothing else. Proxmox is connected to my MGMT VLAN through one ethernet port, while all of my VM's are bridged to the CyberArena VLAN using a separate port.
I ended up reviewing and rewriting my firewall rules for this VLAN and did some tests trying to break out of it to access any other devices on other VLAN's. Once I felt confident, I opened all the required ports by creating a couple of alias's (One for TCP and the other for UDP) in pfSense to quickly toggle them all on or off.
I will be writing up a full report/post for this experiment which I ran for 3 days total before closing all the ports and changing my public IP address for good measure. There are some items I need to learn more about before I feel confident going through the large amount of data captured using this Honey pot suite. For now I will leave a few of the many screenshots I took while monitoring the attacks.
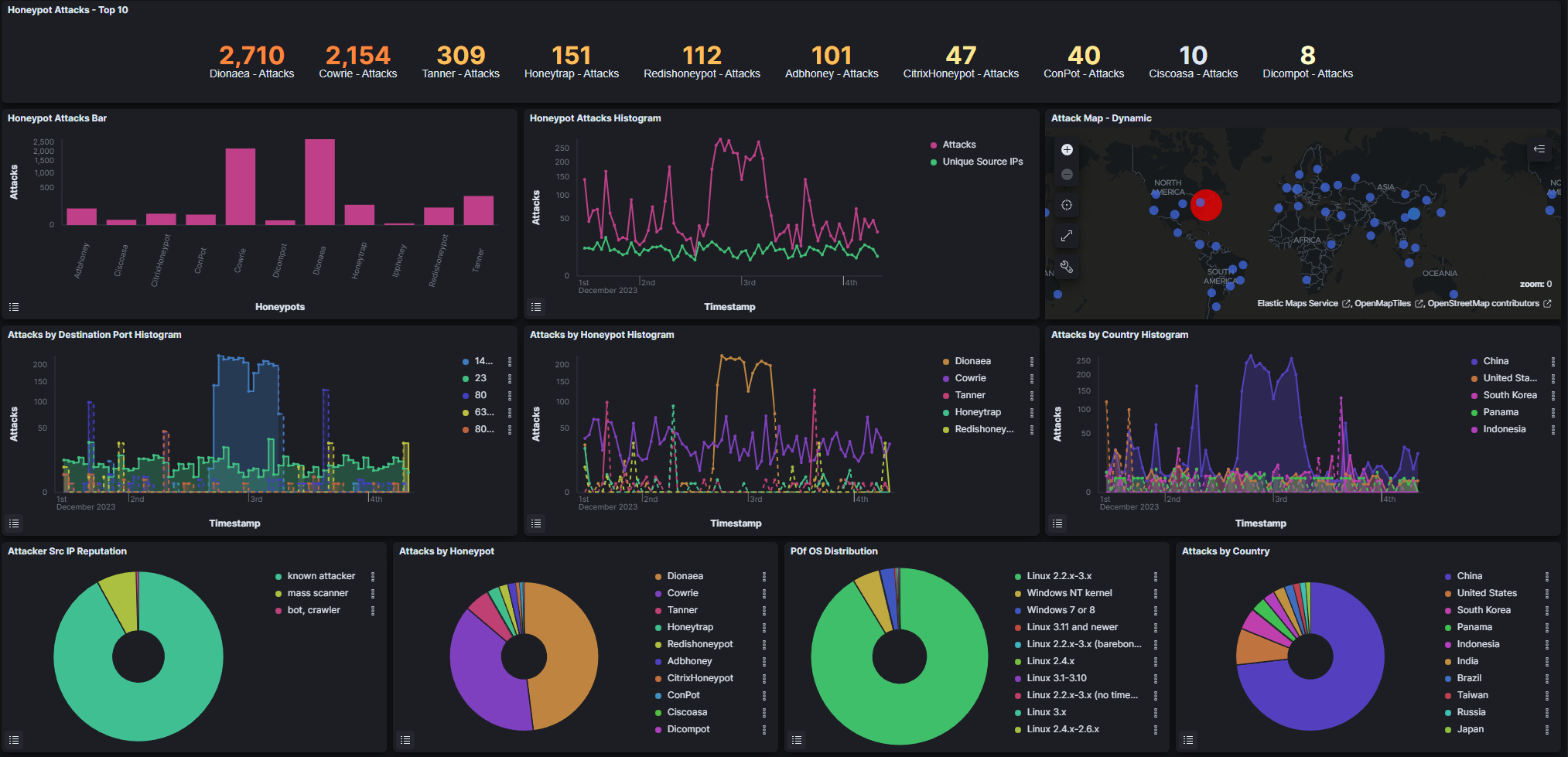
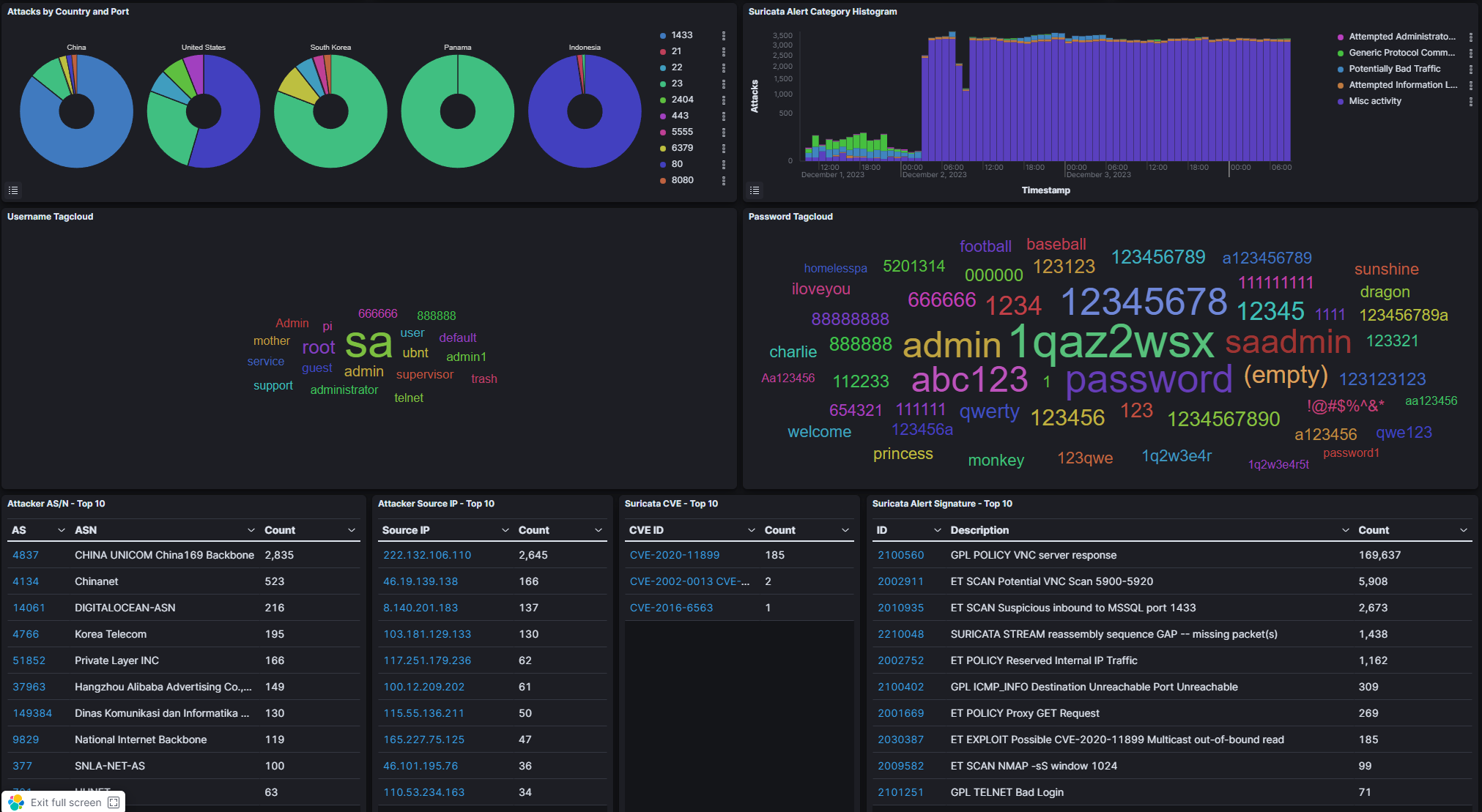
Wrap up
Since I wanted to catch up on everything I have been working on in my homelab, I will also add a few other things that have been taking up my free time. So far I have not posted any of my electronic projects here and I think that might change going into this next year. I want to do away with my portfolio and just keep the blog to post things I'm learning and building.
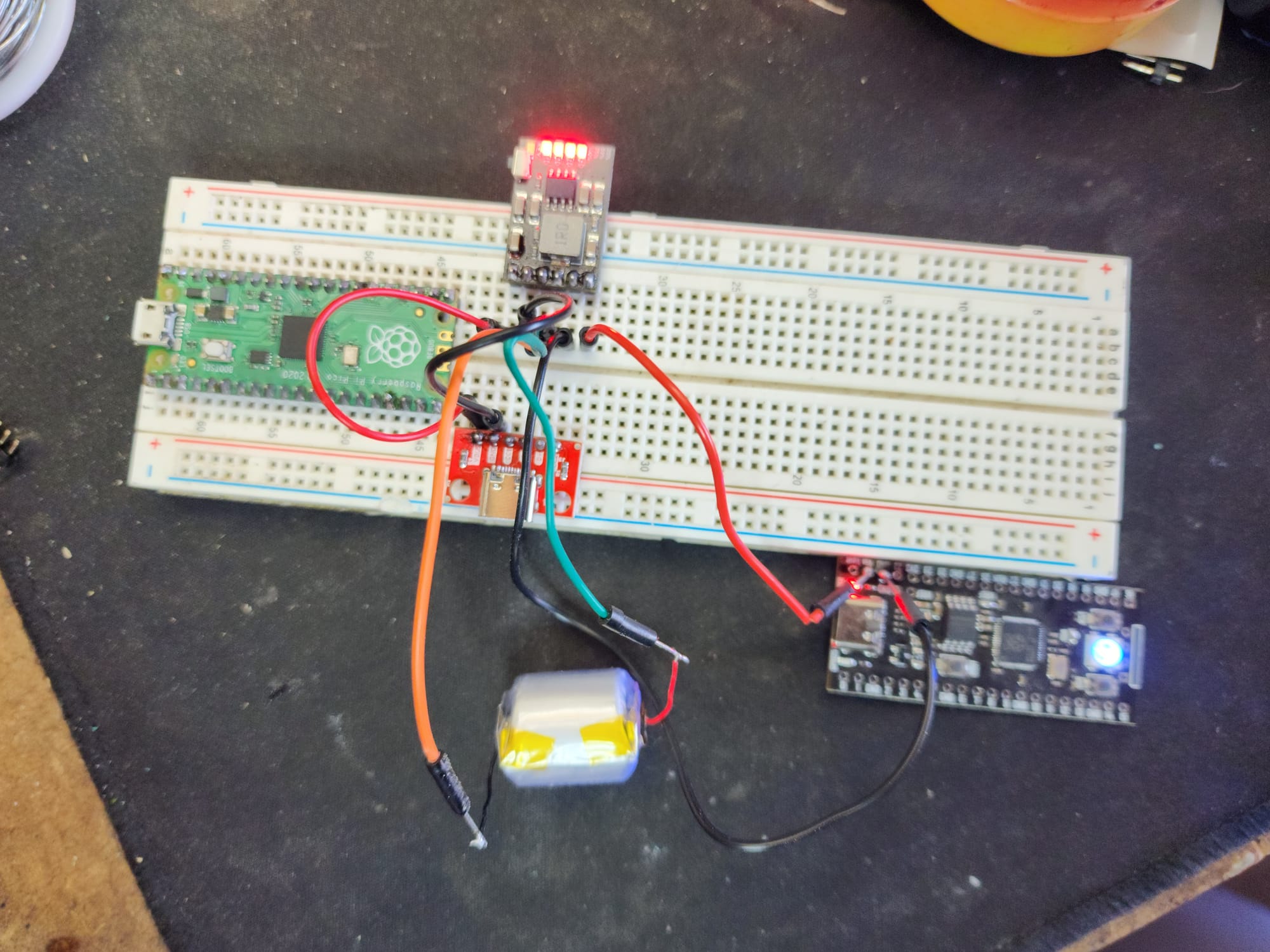
Electronics Projects - I have always enjoyed working with electronics and recently I was working on using the batteries from "disposable" vapes as batteries for small projects. The batteries I've found are small but very much re-usable. In the picture I'm showing the disassembled vape and some components wired in a way to run something off the battery while having a USB-C port for charging as well. I want to use these batteries to run some smaller projects although I'm curious to know how long one of these will run a Pi Zero. the batteries I've found so far have been 3.7V and 500mAh.
I have also been working with radio frequencies and Wi-Fi hacking. I have use Raspberry Pi's in the past for this and there are so many projects using the Pi and/or microcontrollers. One in particular I had a lot of fun with decoding radio signals from remotes is the cc1101-tool from Adam Loboda, which uses an ESP 32 flashed with his project and a CC1101 transceiver for working with the signals. He has a few interesting projects on GitHub and also posts videos on his YouTube Channel.


Soon I would like to combine some components into a handheld device that can be used as a mobile platform for auditing Wi-Fi and radio devices, experimenting with radio frequencies and hardware configurations.
And that's most of what I am working on. I usually pick up smaller side projects but I won't bore you with all those. Once something turns into a larger project, I will document and post here.
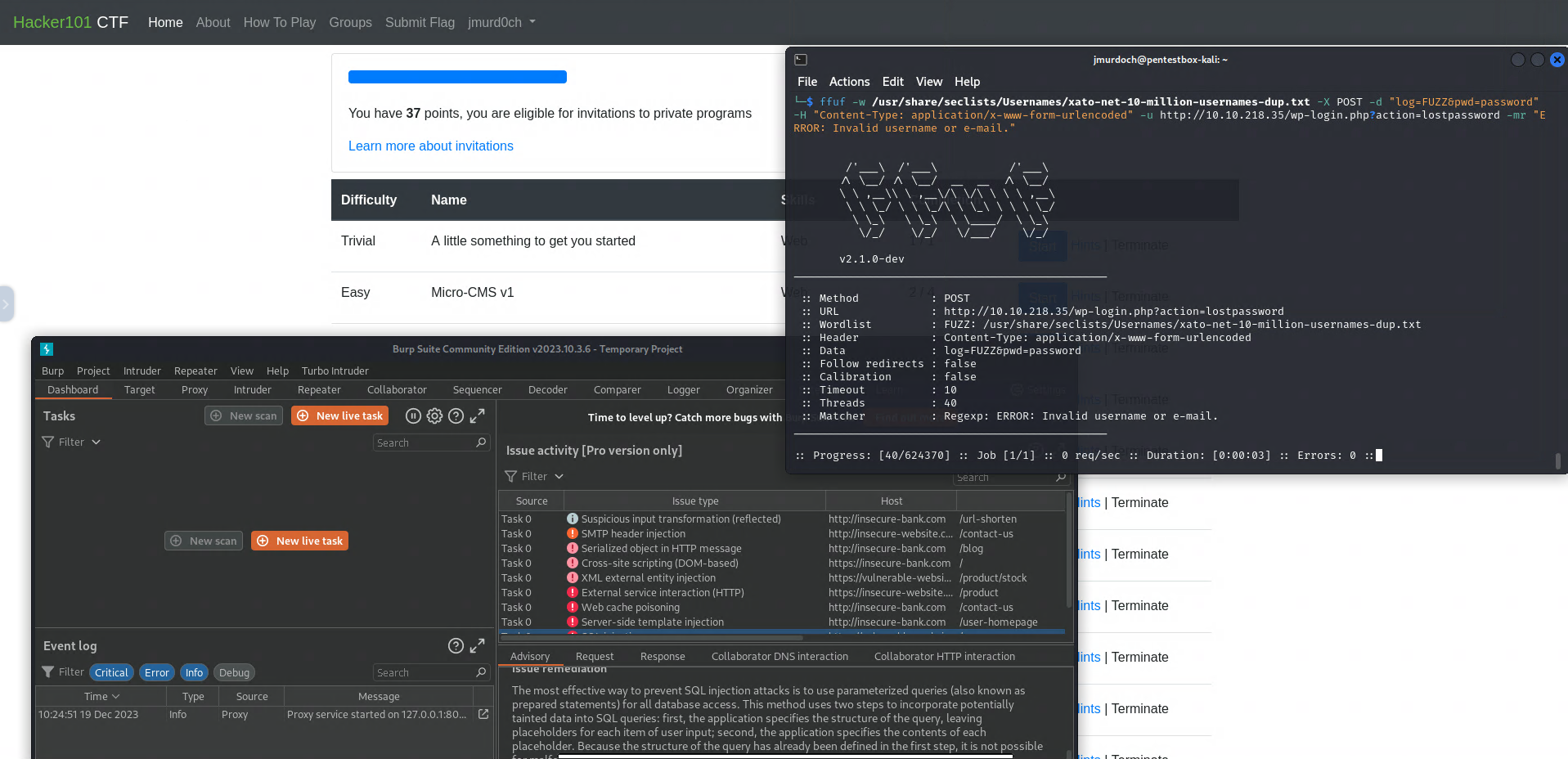
CTF's and Web Application Pentesting - I have been taking time to learn about Web app pentesting by going through the Bug Bounty path at Hack The Box Academy as well as CTF's from Hacker 101 and others. When I'm frustrated or hit a brick wall while learning something new and need some time to think, I enjoy working through these CTF challenges and learning about Bug Bounties. This is something I want to continue pursuing so you will most likely see posts and/or write-ups in the future.
I've enjoyed learning more about the tools such as Burp suite, ZAP, and CLI tools like FFUF and Dirb to name just few. Bug Bounty programs are very interesting to me and I can't wait to delve deeper into them.
Thank you for checking out my blog. I hope you have a great end of the year, stay safe!
